 Remove computer from any computer case, computer box, computer packaging, or computer bag. Do not leave us with your computer case, computer packaging box, or computer bag. We do not have room to store this stuff for you.
Remove computer from any computer case, computer box, computer packaging, or computer bag. Do not leave us with your computer case, computer packaging box, or computer bag. We do not have room to store this stuff for you.
Remove all usb drives, usb dongles, external hard drives, blue tooth dongles, and any extraneous hardware such as mouse, keyboards, printers, speakers, microphones, headphones, and monitors, attached to your computer or device before dropping off at South City Computer.
Remove all CD/DVD or other media from drives. We can not be responsible for your 2nd season of “Friends” DVD left in the DVD drive so please remove it before dropping it off at South City Computer.
Bring the power cord with your laptop, tablet, phone, all-in-one computer, or device. Most desktops use a standard power cord. Bring it, and the service technician will instruct you whether or not South City Computer will need it to perform your computer repair service.
Ensure your computer is clean and free of food, dust, and other debris. We know that most people eat, drink, and even pick their nose at their computer. Please do not bring us a computer covered in food, dust, boogers, and other unspeakable fluids! We are trying to provide you computer repair service, we are not a computer cleaning service. We will disinfect the computer at the time of drop off, however we do not want to have to scrub boogers and debris from the keyboard and cracks of your computer. If your computer is exceptionally disgusting, we may have to charge you a cleaning fee.
Let us know if you or somebody else is sick and has used the computer or if you are bringing your computer in because you or somebody else vomited on/in it. Let us know ahead of time so we can make special preparations to handle your computer with latex hospital gloves and respiratory masks.
Let us know if you dropped your device into a toilet or other unsanitary conditions so that we can prepare to handle your device accordingly with latex hospital gloves.
Provide the service technician clear and accurate description of your issue. Be sure to include what you were doing when the computer stopped working, any error messages you recall, any strange pop-ups, any strange behaviors or sounds your recall coming from the computer, any programs you installed or uninstalled before the issue started, also if there were any other anomalies such as power outages or electrical storms that could be related to the computer issue.
Provide all passwords and user accounts that South City Computer will need to access the computer.
Let us know if you need the data backed up on the computer. If data needs to be backed up, provide the service technician all files, file types, directories, and file names that you would like attempted to be backed up.
Inform the service technician of any programs you use that put their data files in places outside the Windows user directory such as Quick Books, Quicken, or Microsoft Outlook.
Be prepared to wait for service. Our typical turn around on a computer diagnosis is 2 to 5 business days. If you need expedited service talk to a support service technician about the options South City Computer offers customers who need computer repair service fast! Also, South City Computer Club Members always enjoy concierge services and get moved to the front of the line on most computer repair services. Don’t call or email constantly to check the status of your computer repair, this does not speed things up, as we are answering your phone calls and emails instead of repairing computers.
Bring cash, check, or credit/debit card to make the initial payment for service. We cannot begin work on your computer repair service until we receive payment up front.
Please know that we do not offer refunds on any payment you make to South City Computer, even if you choose to forgo the initial diagnosis or other service. If you are professional, friendly, courteous, and easy to do business with, we will most likely offer you in-store credit if you decide to not move forward with a repair, but this is not a guaranteed, and totally up to managements discression.

 The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer.
The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer. With the holidays only a few weeks away you may be scouring the Internet or going from big box store to big box store in St. Louis looking for some ideal tech gifts. The following are 5 really cool new tech gift ideas that could be just the right gift for the tech savvy person or the not so tech savvy person on your gift giving list.
With the holidays only a few weeks away you may be scouring the Internet or going from big box store to big box store in St. Louis looking for some ideal tech gifts. The following are 5 really cool new tech gift ideas that could be just the right gift for the tech savvy person or the not so tech savvy person on your gift giving list.
 You’ve probably heard before that using your computer too close to bedtime can cause sleep loss. Many have dismissed this as something of an urban legend, or something your mother would tell you because she thinks that you’re not getting enough sleep. If that’s true in your case, don’t let her see
You’ve probably heard before that using your computer too close to bedtime can cause sleep loss. Many have dismissed this as something of an urban legend, or something your mother would tell you because she thinks that you’re not getting enough sleep. If that’s true in your case, don’t let her see 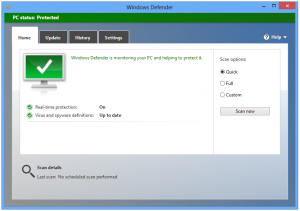 Often we are asked what anti virus software to use? While it is totally preference at this point since most anti-virus software’s do the task of scanning and monitoring your computer for suspicious programs, viruses and malware, not all anti virus softwares are free. We usually recommend a free anti-virus software since subscription renewals can be easily ignored, and it is better to have current anti-virus definitions than to have none at all.
Often we are asked what anti virus software to use? While it is totally preference at this point since most anti-virus software’s do the task of scanning and monitoring your computer for suspicious programs, viruses and malware, not all anti virus softwares are free. We usually recommend a free anti-virus software since subscription renewals can be easily ignored, and it is better to have current anti-virus definitions than to have none at all.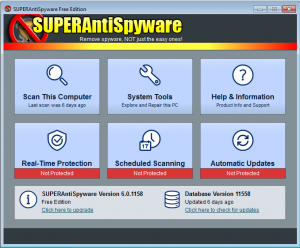 SUPERAntiSpyware is a “Freeware” software application which can detect and remove spyware, adware, trojan horses, rogue security software, computer worms, rootkits, parasites and other potentially harmful software applications. Although it can detect malware, SUPERAntiSpyware is not designed to replace antivirus software.
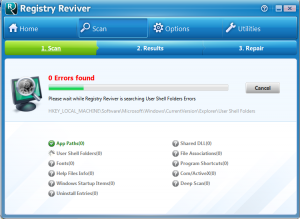
SUPERAntiSpyware is a “Freeware” software application which can detect and remove spyware, adware, trojan horses, rogue security software, computer worms, rootkits, parasites and other potentially harmful software applications. Although it can detect malware, SUPERAntiSpyware is not designed to replace antivirus software. Watch out for a new piece of malware and spyware that has been popping up on many computers that are coming into our computer repair shop in St. Louis this past couple months. Malware is short for “malicious software” and is unwanted software that can hijack certain functions of your computer, steal sensitive information, and can put your personal information and data at risk. Malware is usually bundled with tojans, worms, rootkits, spyware, adware, ransomware and viruses. Unfortunately most malware can be very tricky to remove. The new malware we have been seeing has no easy removal method at this time and reeks havoc on the computer’s Windows registry. The Windows registry is the place where Windows stores Operating System and program configurations.
Watch out for a new piece of malware and spyware that has been popping up on many computers that are coming into our computer repair shop in St. Louis this past couple months. Malware is short for “malicious software” and is unwanted software that can hijack certain functions of your computer, steal sensitive information, and can put your personal information and data at risk. Malware is usually bundled with tojans, worms, rootkits, spyware, adware, ransomware and viruses. Unfortunately most malware can be very tricky to remove. The new malware we have been seeing has no easy removal method at this time and reeks havoc on the computer’s Windows registry. The Windows registry is the place where Windows stores Operating System and program configurations.  Are you looking to support local business? We offer local computer repair in St. Louis offering computer repair, new and refurbished computer sales, and south saint louis business IT services to individuals, organizations, churches and businesses. We are specialized in computer repair, data recovery, virus removal, malware removal, networks, computer support, screen repair and replacement, motherboard repair and replacement, as well as VOIP phone systems, and smartphone/iPhone/Android iPad/tablet repair.
Are you looking to support local business? We offer local computer repair in St. Louis offering computer repair, new and refurbished computer sales, and south saint louis business IT services to individuals, organizations, churches and businesses. We are specialized in computer repair, data recovery, virus removal, malware removal, networks, computer support, screen repair and replacement, motherboard repair and replacement, as well as VOIP phone systems, and smartphone/iPhone/Android iPad/tablet repair.