 If you are typing your password and press Enter and see the error message “The User Profile Service failed the logon” and “The user profile cannot be loaded”, and then are returned to the logon screen, your Windows user profile may have become corrupt.
If you are typing your password and press Enter and see the error message “The User Profile Service failed the logon” and “The user profile cannot be loaded”, and then are returned to the logon screen, your Windows user profile may have become corrupt.
A Windows user profile is a collection of settings that make the computer look and work the way you want it to. The Windows user profile contains your personalized settings for desktop backgrounds, screen savers, mouse pointer preferences, sound settings, and other Windows features.
While it is hard to say exactly why Windows user profiles become corrupt there are a few more common reasons that this happens. The antivirus software on the computer could have corrupted to profile by running a scan before the user profile was actually logged into the computer. Another reason the user profile can be corrupted is malware has messed up the registry settings for the user profile, and it no longer works and has become corrupt.
If you have recently attempted to log on to Windows and received an error message that says that your user profile might be corrupted, there are a few steps you can try to repair it.
WARNING: You should create a backup of your user files before attempting to fix your user profile. Contact a local computer repair store if you need help to backup your data.
Try a reboot
The first attempt you can try to fix your Window user profile is to simply reboot the computer. Sometimes a reboot will fix the issue, and you will be able to log in to the profile when the computer is completely rebooted.
Try creating an alternative user profile
If rebooting the computer doesn’t seem to fix the corrupt user profile, then a quick and easy fix is to create a new user profile on the Windows computer, and then copy the files from the existing profile to the new one. While this should get you back up and running you will lose all of the Windows user personalized settings by doing this such as the desktop, screensaver, etc. You will have all of your user files ie. Documents, Videos, Pictures, Music, etc.
To accomplish creating a new Windows user you will need to log in to an administrator account on the computer. If you have another administrator user account already created you could log in to this account, however if you only had one administrator account on the computer you will need to activate the default Windows user account.
First boot the computer into Safe Mode by pressing F8 during bootup. On the Windows loading screen choose Safe Mode from the menu. When the Windows desktop is launched, choose the start menu and search for cmd. When the computer finds the command prompt program right click and run the program as administrator.
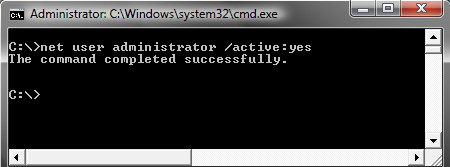
When the command prompt program is launched type in the command: net user administrator /active:yes
This will activate the “hidden” administrator account on the computer after the computer is rebooted.
You should see a message that the command completed successfully. Log out, and reboot the computer and you’ll now see the Administrator account as a choice.
Log in with the new Administrator account. If you are prompted for a password it is probably not set and by not typing anything in the password input should log into the account.
When you are logged in as the Administrator account:
- Open User Accounts by clicking the Start button Picture of the Start button, clicking Control Panel, clicking User Accounts and Family Safety, and then clicking User Accounts.
- Click Manage another account. Administrator permission required If you’re prompted for an administrator password or confirmation, type the password or provide confirmation.
- Click Create a new account.
- Type the name you want to give the user account, click an account type, and then click Create Account.
- Restart the PC.
When the computer has rebooted
- Log on as the administrator user.
- Open the My Documents folder by clicking the Start button Picture of the Start button, and then clicking Computer. Double-click the hard disk drive that Windows is installed on (it’s usually your C: drive), double-click Users, double-click the folder with the name of the corrupt user profile account, and then double-click My Documents.
- Click the Tools menu, and then click Folder Options.
- If you don’t see the Tools menu, press Alt.
- Click the View tab, and then click Show hidden files, folders, and drives.
- Clear the Hide protected operating system files check box, click Yes to confirm, and then click OK.
- Locate the C:\Users\Old_Username folder, where C is the drive that Windows is installed on, and Old_Username is the name of the profile you want to copy files from.
- Select all of the files and folders in this folder, except the following files:
Ntuser.dat
Ntuser.dat.log
Ntuser.ini - Click the Edit menu, and then click Copy.
- If you don’t see the Edit menu, press Alt.
- Locate the C:\Users\New_Username folder, where C is the drive that Windows is installed on, and New_Username is the name of the new user profile you created.
- Click the Edit menu, and then click Paste.
- If you don’t see the Edit menu, press Alt.
- Log off, and then log back on as the new user.
- To fix the user profile, click Start and type regedit into the search box and press Enter.
- In Registry Editor navigate to:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList - Click each S-1-5 folder and double-click the ProfileImagePath entry to find out which user account it relates to.
- Once you have located the folder for the corrupt profile (and it doesn’t have a .bak ending), double-click RefCount and change the Value data to 0 and click Ok.
- Now double-click on State and make sure the Value data is again 0 and click Ok.
- Close regedit and restart your PC. You should now be able to log into your account.
If you have e‑mail messages in an e‑mail program, you must import your e‑mail messages and addresses to the new user profile before you delete the old profile. If everything is working properly, you can delete the old profile.
Attempt to salvage the corrupt user profile
If you want to attempt to salvage your old Windows user profile, you can try this more complex solution:
Restart your PC and boot into Safe mode by pressing F8 before you see the Windows loading screen and choosing Safe Mode from the menu that appears.
If you continue to get the corrupt user profile message you will need to attempt to create an alternative user profile and copy the data from the corrupt user profile into it.
If you are unable to successfully create a new user profile, bring your computer to South City Computer or a local computer repair store near you.

 Joe Vaccaro is the Alderman of the 23rd Ward in Saint Louis City. He is very involved with the community and frequently passes on tips and information about dangers to people in the community.
Joe Vaccaro is the Alderman of the 23rd Ward in Saint Louis City. He is very involved with the community and frequently passes on tips and information about dangers to people in the community. Phishing, pronounced like “fishing”, is where a malicious website is set up in order to trick users into divulging personal information such as log in credentials, credit card, banking, or other private information. These website can look very convincing, mimicking a bank website, or a credit card website, or even a social media website log in. The website is meant to fool the user into divulging private information. Many of the sites will actually take in the information that is typed in the form, and then send the user over to the real login website, so that the user thinks that they just didn’t put in their log in information correctly, and never realize that they just gave away their personal information to a scammer.
Phishing, pronounced like “fishing”, is where a malicious website is set up in order to trick users into divulging personal information such as log in credentials, credit card, banking, or other private information. These website can look very convincing, mimicking a bank website, or a credit card website, or even a social media website log in. The website is meant to fool the user into divulging private information. Many of the sites will actually take in the information that is typed in the form, and then send the user over to the real login website, so that the user thinks that they just didn’t put in their log in information correctly, and never realize that they just gave away their personal information to a scammer. 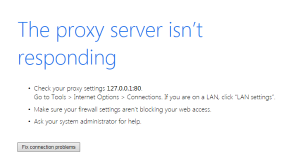 One of the more common computer issues we see because of malware is a misconfiguration Proxy Server connection setting in the browser. You may be able to do a quick fix to get your Internet connection back up and running, however if this has gotten set and you don’t recall doing it, this is probably because your computer is infected with malware or a virus.
One of the more common computer issues we see because of malware is a misconfiguration Proxy Server connection setting in the browser. You may be able to do a quick fix to get your Internet connection back up and running, however if this has gotten set and you don’t recall doing it, this is probably because your computer is infected with malware or a virus. While there is no fool proof way to avoid being hacked, here is a list of tips in order to avoid from getting hacked.
While there is no fool proof way to avoid being hacked, here is a list of tips in order to avoid from getting hacked. As banks have beefed up their cyber security in the recent months after a JP Morgan Chase announced a data breach, hackers seemed to have turned their sights onto healthcare providers and insurance companies. Last week medical insurance company Anthem publicly apologized to its customers for a data breach that could have leaked over 80 million records that included names, addresses, phone numbers, and social security numbers. The company has described the data breach as a “very sophisticated external cyber-attack”. Anthem is still investigating whether the hackers were able to obtain any sensitive medical records or patient history. The data breach could be one of the largest in history.
As banks have beefed up their cyber security in the recent months after a JP Morgan Chase announced a data breach, hackers seemed to have turned their sights onto healthcare providers and insurance companies. Last week medical insurance company Anthem publicly apologized to its customers for a data breach that could have leaked over 80 million records that included names, addresses, phone numbers, and social security numbers. The company has described the data breach as a “very sophisticated external cyber-attack”. Anthem is still investigating whether the hackers were able to obtain any sensitive medical records or patient history. The data breach could be one of the largest in history. Are you getting a pop-up in Internet Explorer with the following:
Are you getting a pop-up in Internet Explorer with the following: Remove computer from any computer case, computer box, computer packaging, or computer bag. Do not leave us with your computer case, computer packaging box, or computer bag. We do not have room to store this stuff for you.
Remove computer from any computer case, computer box, computer packaging, or computer bag. Do not leave us with your computer case, computer packaging box, or computer bag. We do not have room to store this stuff for you.  The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer.
The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer. Every few years desktops, laptops, smart phones, tablets and electronic equipment become “obsolete”. The shiny new Apple iPhone you got today will be an obsolete piece of junk in a few years, and in turn will need to be disposed of responsibly. Unfortunately most people do not consider this when they purchase their new technology device, and this lack of thought is causing a real problem for the environment.
Every few years desktops, laptops, smart phones, tablets and electronic equipment become “obsolete”. The shiny new Apple iPhone you got today will be an obsolete piece of junk in a few years, and in turn will need to be disposed of responsibly. Unfortunately most people do not consider this when they purchase their new technology device, and this lack of thought is causing a real problem for the environment.