 The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer.
The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer.
1. Have an anti-virus program installed and running. Having anti-virus protection can help to reduce your risk of getting a computer virus. But do not rely too heavily on these programs, as many new viruses are still unknown to the anti-virus programs and there is always a lapse in full protection. Many new viruses have not been documented and released in the most recent virus definitions. Also most anti-virus software only do system scanning and do not do real-time system monitoring, and the ones that do offer real-time system monitoring may not always catch viruses getting installed on the computer.
2. Keep anti-virus software up-to-date with the latest virus definitions. Just having an anti-virus software installed on your computer is not enough to protect you from the latest virus and computer threats. Keep your anti-virus definitions up-to-date with the latest virus definitions. It is recommended to run anti-virus definitions updates on a daily basis to ensure the most effective anti-virus protection.
3. Keep your operating system up-to-date. This means run those pesky Windows Updates whenever your computer prompts you to. Updates oftentimes contain security patches and fixes that have been identified by the software distributor as vulnerabilities. It is best to set your computer to automatically update at a time that you would most likely not be using your computer, such as 3AM. Just remember to leave your computer on and connected to the Internet overnight to install these critical updates.
4. Only open email attachments from trusted sources and in believable situations. Most people get computer viruses by downloading attachments to emails. The attachments can seem legitimate such as a attached document, media file, or picture sent to you from friends or family. However you should be very careful not to download a virus. Sometimes friends, family, or coworkers email accounts can get hacked and will send out malicious software. Always check the file extension that is attached to an email before downloading it onto your computer. If the file extension is a .exe, .bat, .msi, .zip, .msm, .msp, .mst, .idt, .cub, .pcp file this could be a malicious software application. Common pictures file types are .jpg, .png, .gif, .tif, .bmp, and some common document file types are .doc, .docx, .xls, .xlsx, .odt, .txt. If you get an email with a strange file attached to it that doesn’t look like any of these common extensions, it is probably best to first verify with the trusted sender that they indeed sent the file. Also never click on links sent in emails that seem vague like “hey look at this link” or “click here to see my pics”.
5. Never install programs from the Internet that claim to fix a computer issue. While it may seem like a good idea to ask “Google” to fix your computer issue for you. Unfortunately most websites that claim to fix a computer issue by installing a program are not legitimate and are likely just fishing websites to get spam-ware, and other malicious software installed on your computer. Always take your computer to a legitimate computer repair business to fix your computer issue, and never search for a fix using a software program from the Internet.
6. Never illegally download pirated software, music and movies. Most illegal pirating networks, file sharing networks, and file link website will contain malicious software disguised as the newest software, movies or pop music albums. Always purchase software, music, and movies legally to avoid getting a virus from these untrusted file sources.
7. Do not try to install extraneous video and audio codecs. Sometimes you may find a file that has a strange extension. It seems logical to try to find a audio or video codec, or other program that could read this extension, however it is more likely that you would download and install a virus than the actual solution for your file type.
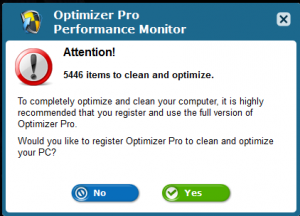
8. Do not install programs that claim to enhance the performance of your computer. There are some programs online that will claim to speed up your computer, or enhance the performance of your computer, or even promise to enhance the graphics capabilities of a computer. These are most likely untrusted websites that try to trick you into installing spam-ware, ransom-ware, malicious programs, and viruses onto your computer.
9. Do not install illegal software on your computer. You may find yourself in situations where a friend, family or other acquaintance has a “hot” copy of a popular software app like Microsoft Office or Adobe Creative Suite for FREE. If it sounds too good to be true…well then it probably is. Do not be fooled, these types of software cost hundreds to thousands of dollars, and the pirated “hot” copies tend to be packaged with malicious software. Always purchase software legally from trusted software distributors. Never install “hot” or “cracked” versions of a licensed software or service.
10. Do not click on pop-ups! Really, DON’T DO IT! Some pop-ups mimic Windows operating system alerts, and can look very convincing at times. Here are a few dead give-aways that you may have an untrusted pop-up:
- has strange unfamiliar icons
- the error message has improper English
- the pop-up box has a message in it promissing to fix your computer issues
- the pop-up moves around
- the pop-up says your computer is infected with a virus
Even the most cautious computer user can sometimes be fooled into installing a computer virus. If you think you may have a computer virus on your computer, contact South City Computer for a tech visit today.
 Lenovo recently released a product security advisory about a man-in-the-middle attack vulnerability that exists on some of the Lenovo Notebook laptop models sold by the company between Jan 2014 until Feb 2015.
Lenovo recently released a product security advisory about a man-in-the-middle attack vulnerability that exists on some of the Lenovo Notebook laptop models sold by the company between Jan 2014 until Feb 2015.
 Joe Vaccaro is the Alderman of the 23rd Ward in Saint Louis City. He is very involved with the community and frequently passes on tips and information about dangers to people in the community.
Joe Vaccaro is the Alderman of the 23rd Ward in Saint Louis City. He is very involved with the community and frequently passes on tips and information about dangers to people in the community. Phishing, pronounced like “fishing”, is where a malicious website is set up in order to trick users into divulging personal information such as log in credentials, credit card, banking, or other private information. These website can look very convincing, mimicking a bank website, or a credit card website, or even a social media website log in. The website is meant to fool the user into divulging private information. Many of the sites will actually take in the information that is typed in the form, and then send the user over to the real login website, so that the user thinks that they just didn’t put in their log in information correctly, and never realize that they just gave away their personal information to a scammer.
Phishing, pronounced like “fishing”, is where a malicious website is set up in order to trick users into divulging personal information such as log in credentials, credit card, banking, or other private information. These website can look very convincing, mimicking a bank website, or a credit card website, or even a social media website log in. The website is meant to fool the user into divulging private information. Many of the sites will actually take in the information that is typed in the form, and then send the user over to the real login website, so that the user thinks that they just didn’t put in their log in information correctly, and never realize that they just gave away their personal information to a scammer.  While there is no fool proof way to avoid being hacked, here is a list of tips in order to avoid from getting hacked.
While there is no fool proof way to avoid being hacked, here is a list of tips in order to avoid from getting hacked. As banks have beefed up their cyber security in the recent months after a JP Morgan Chase announced a data breach, hackers seemed to have turned their sights onto healthcare providers and insurance companies. Last week medical insurance company Anthem publicly apologized to its customers for a data breach that could have leaked over 80 million records that included names, addresses, phone numbers, and social security numbers. The company has described the data breach as a “very sophisticated external cyber-attack”. Anthem is still investigating whether the hackers were able to obtain any sensitive medical records or patient history. The data breach could be one of the largest in history.
As banks have beefed up their cyber security in the recent months after a JP Morgan Chase announced a data breach, hackers seemed to have turned their sights onto healthcare providers and insurance companies. Last week medical insurance company Anthem publicly apologized to its customers for a data breach that could have leaked over 80 million records that included names, addresses, phone numbers, and social security numbers. The company has described the data breach as a “very sophisticated external cyber-attack”. Anthem is still investigating whether the hackers were able to obtain any sensitive medical records or patient history. The data breach could be one of the largest in history.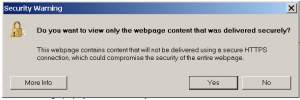 Are you getting a pop-up in Internet Explorer with the following:
Are you getting a pop-up in Internet Explorer with the following: The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer.
The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer.
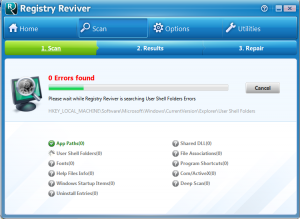
 Watch out for a new piece of malware and spyware that has been popping up on many computers that are coming into our computer repair shop in St. Louis this past couple months. Malware is short for “malicious software” and is unwanted software that can hijack certain functions of your computer, steal sensitive information, and can put your personal information and data at risk. Malware is usually bundled with tojans, worms, rootkits, spyware, adware, ransomware and viruses. Unfortunately most malware can be very tricky to remove. The new malware we have been seeing has no easy removal method at this time and reeks havoc on the computer’s Windows registry. The Windows registry is the place where Windows stores Operating System and program configurations.
Watch out for a new piece of malware and spyware that has been popping up on many computers that are coming into our computer repair shop in St. Louis this past couple months. Malware is short for “malicious software” and is unwanted software that can hijack certain functions of your computer, steal sensitive information, and can put your personal information and data at risk. Malware is usually bundled with tojans, worms, rootkits, spyware, adware, ransomware and viruses. Unfortunately most malware can be very tricky to remove. The new malware we have been seeing has no easy removal method at this time and reeks havoc on the computer’s Windows registry. The Windows registry is the place where Windows stores Operating System and program configurations.