The internet is a big place — and offers what is likely the widest variety of material that could ever be thought of. Certainly some of this information is good and useful, ranging from scholarly articles and thesis papers to tutorials to help the Average Joe with everyday problems. The amount of good material on the Internet is a compelling reason to grant your children access to it, not to mention the fact that it has become essential in doing research for both school and personal projects.
Naturally, though, there are some things online that ought to be avoided. This article will focus on those things that don’t pose a risk to the average adult, but can be a danger when it comes to teenage boys.
1. Downloading “free” programs that leave your computer in a nasty state
While many adults only use a computer for getting work done, checking email, and other simple tasks, this generation tends to be much more attached to computers and other devices. Of course, this means that these persons would want to extend their computers’ capabilities, and this often means downloading more programs. While there are many awesome programs out there that will help your teenager become more adept at using the computer to do constructive things, there are also programs that claim to do such things but are really just a way for a virus to get in. Common offenders include programs that claim to:
- Download videos from YouTube or other websites
- Allow free access to movies or music that one would typically pay for
- Automatically fix problems on the computer
- Install Adobe Flash, Java, Silverlight, or other runtimes.
What can you do?
- Monitor your computer for the installation of new programs:
If you see any new programs on your computer that you don’t remember installing, consult an expert to see if the program is legitimate or not. Take note that Windows will often inform you of a new program being installed by highlighting the “All Programs” item on the start menu in yellow or red. - Direct your son to sourceforge.com, a reputable website that offers a plethora of free programs from various developers.
- Install runtimes from legitimate sources beforehand, so that your son won’t download a fake version when he runs into a problem. Here are the legitimate websites for obtaining some of the most common runtimes.
Adobe Flash Player: get2.adobe.com/flashplayer
Java: www.java.com
Silverlight: www.microsoft.com/silverlight
Using BitTorrent to illegally get copyrighted material
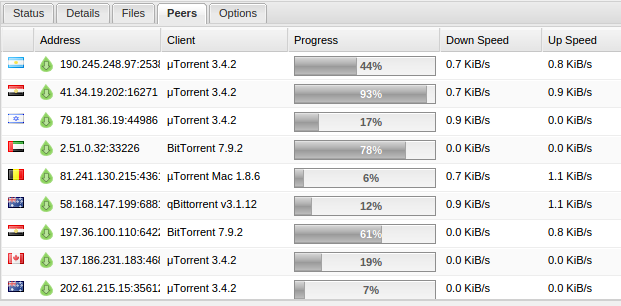
Torrent client showing the IP addresses of everyone connected.
Piracy is one of the biggest problems today. It’s not limited to use by just teenagers, but it’s an important thing to remember that it may be happening on your computer, even if it’s not you doing it. Most pirated content is distributed by using the BitTorrent protocol, which allows you to download the file from a variety of other people that have it. Most Torrent clients also make your computer one of the “seeds,” meaning that you will be one of the sources that other people download content from, therefore meaning your computer is not just illegally downloading copyrighted material, but also distributing it. While BitTorrent is one of the more obscure protocols out there, it does absolutely nothing to hide your identity — that’s simply not what it is meant to do. As you can see by the screenshot above, your IP address, a unique identifier for your internet connection, is shared with everyone else connected, meaning it’s easy for law enforcement to look in and see who’s downloading any given file.
What you can do
BitTorrent requires a client program to be installed on the computer. If you notice something that appears to be a torrent client, consult with your son and take the computer to an expert to have it removed. BitTorrent clients often have the word “torrent” in the name. Common ones include BitTorrent, uTorrent, Deluge, and BitLord.
3. Accessing Pornography
You’re entitled to your own opinion on the moral implications of porn, but we’re here to tell you that there is more to it than that. Porn typically comes riddled with viruses and other malware that can negatively effect your computer. The worst cases occur when pornography is downloaded from the internet, which is typically done using the BitTorrent protocol as described in the last section. Since it’s actually loaded into your computer, there are many exploits that it will try to take advantage of. Weaker attacks will be stopped by Antivirus software, but often, antivirus software will not catch the malicious software until too late. Incognito mode, or similar browser functions will not protect your computer. The other issue that tends to occur is the accessing of child pornography. While it’s natural for a 14-year old to want to view pornography with 14-year olds in it, this is still illegal, and the owner of the internet connection, typically the parents, will be the ones held responsible.
What you can do
First of all, avoid pornography that requires a download. This is not foolproof, but it gives you a better chance of avoiding unwanted malware. If your computer is regularly used to access pornography, it’s recommended that you take it in for regular check-ups. This will ensure that no malware that is installed can develop into a headache in the future.
If you think that pornography has been downloaded using your machine, it is best to bring it to an expert for a checkup. This can be somewhat embarrassing, but the malware typically does not show where it came from. Our job is to simply remove the malware, not play detective and try to figure out what you were doing when it got onto your computer.
South City Computer also offers discrete data destruction, providing complete, irrevocable removal of any unwanted files from your computer.
