 Earlier this year cyber security software company Kapersky announced the discovery of a cyber intrusion that affected many of it’s internal computer systems which initiated a large scale investigation. They believe the virus penetrated their systems through an email attachment sent to an employee at the company. From there the virus moved stealthily through the company’s computer network targeting it’s customer’s computer networks and collecting information. Instead of removing the virus Kapersky monitored the virus on their systems in an attempt to better understand its function and purpose.
Earlier this year cyber security software company Kapersky announced the discovery of a cyber intrusion that affected many of it’s internal computer systems which initiated a large scale investigation. They believe the virus penetrated their systems through an email attachment sent to an employee at the company. From there the virus moved stealthily through the company’s computer network targeting it’s customer’s computer networks and collecting information. Instead of removing the virus Kapersky monitored the virus on their systems in an attempt to better understand its function and purpose.
The investigation led to the discovery of a new highly sophisticated malware platform known as Duqu. The platform was developed from one of the most skilled, mysterious and powerful underground groups in malware. The virus is considered to be in the same league of complexity as the “Stuxnet” worm that was discovered in June 2010 by “Symantic” and has been nicknamed the “step-brother of Stuxnet” in the cyber security world. The Stuxnet worm was a malware created to target Iranian nuclear centrifuge control system software and reportedly ruined one-fifth of Iran’s nuclear centrifuges.
The Duqu malware platform was initially discovered in 2011 by Crysys labs in Budapest Hungary. Crysys Labs released a 60 page document to the cyber security world defining it as a cyber threat that was not related to Stuxnet as was initially believed because it was nearly identical to Stuxnet, but seemingly had a completely different purpose.
In 2012 the mysterious group responsible for Duqu seemed to have gone dark, and the Duqu virus seemed to no longer pose a threat, that is, until now.
The Duqu virus attacks Microsoft Windows computers by using a “zero-day-vulnarability” that uses a Microsoft Word document (.doc) to exploit the computer. A win32k font parsing engine actually enables the virus to install onto the victims computer when the victim downloads and tries to open the Microsoft document.
At first Duqu was thought to be targeting industrial control systems like the “Stuxnet” worm, but recent revelations have uncovered a very different purpose for the virus. The virus actually is a form of spyware targeted hotel computer systems where nuclear arms talks with the Iranian government and allied world leaders (p5+1 events) were happening throughout the world.
Costin Raiu, director of the global research and analysis team at Kaspersky, said the virus was packed with more than 100 discrete “modules” that enabled the infected computers to be controlled by someone else. Other modules found were designed to compress video feeds from surveillance cameras, and also target communications from phones to Wi-Fi networks. The attackers would know who was connected to the infected network, allowing them to eavesdrop on conversations and steal electronic information. The virus is also capable of operating two-way microphones in hotel elevators, computers and alarm systems. The virus automatically deposits a small file on the infected computer to enable a way for the attackers to monitor and return to the computer at a later date.
The only question is, who is responsible for this complex and sophisticated eavesdropping attempt? Who would benefit most from this sort of intelligence? Cyber security experts at Kapersky hinted toward involvement from the Isreali government, initially naming the virus “The Duqu Bet”. “Bet” being the second letter of the Hebrew alphabet, but later changed the name to Duqu 2.0. The Israeli government did not claim any involvement in the Duqu malware platform.
The sophistication and dedication of the Duqu group is a testament of just how complex a virus can be all in an attempt to collect information.

 A new destructive virus known as Rombertik avoids detection from most anti-virus software by making a computer unusable by deleting key files on a computer and filling the hard drive with extraneous bytes of data in order to overwhelm the anti-virus software from detecting it.
A new destructive virus known as Rombertik avoids detection from most anti-virus software by making a computer unusable by deleting key files on a computer and filling the hard drive with extraneous bytes of data in order to overwhelm the anti-virus software from detecting it.  Since 2012 a very sophisticated new form of ransom-ware has been infecting millions of Windows computers. CryptoWall, Cryptorbit, and CryptoLocker or Crypto-malware is a Trojan horse that encrypts files on the compromised computer. The malware uses RSA 2048 bit encryption to scramble important data files using public/private key cryptographic technology making the data files unusable. The victim is instructed to pay a hefty ransom fee ranging from $150 to $750 USD using an anonymous bitcoin payment method to purchase the decryption key that will allegedly decrypt the users files. Even if the user pays the ransom, there’s no guarantee that the attacker will provide the decryption key needed to unlock their files.
Since 2012 a very sophisticated new form of ransom-ware has been infecting millions of Windows computers. CryptoWall, Cryptorbit, and CryptoLocker or Crypto-malware is a Trojan horse that encrypts files on the compromised computer. The malware uses RSA 2048 bit encryption to scramble important data files using public/private key cryptographic technology making the data files unusable. The victim is instructed to pay a hefty ransom fee ranging from $150 to $750 USD using an anonymous bitcoin payment method to purchase the decryption key that will allegedly decrypt the users files. Even if the user pays the ransom, there’s no guarantee that the attacker will provide the decryption key needed to unlock their files. 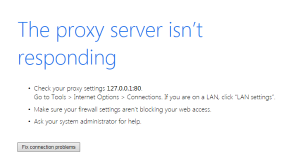 One of the more common computer issues we see because of malware is a misconfiguration Proxy Server connection setting in the browser. You may be able to do a quick fix to get your Internet connection back up and running, however if this has gotten set and you don’t recall doing it, this is probably because your computer is infected with malware or a virus.
One of the more common computer issues we see because of malware is a misconfiguration Proxy Server connection setting in the browser. You may be able to do a quick fix to get your Internet connection back up and running, however if this has gotten set and you don’t recall doing it, this is probably because your computer is infected with malware or a virus. Over the past couple years there have been a number of computer viruses that appear to be anti-virus software. The programs will appear to be scanning your computer and finding many computer viruses, trojans, and worms. Some of these fake anit-virus programs will even turn off the network connection until a payment is made into a phishing website.
Over the past couple years there have been a number of computer viruses that appear to be anti-virus software. The programs will appear to be scanning your computer and finding many computer viruses, trojans, and worms. Some of these fake anit-virus programs will even turn off the network connection until a payment is made into a phishing website. 