 The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer.
The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer.
1. Have an anti-virus program installed and running. Having anti-virus protection can help to reduce your risk of getting a computer virus. But do not rely too heavily on these programs, as many new viruses are still unknown to the anti-virus programs and there is always a lapse in full protection. Many new viruses have not been documented and released in the most recent virus definitions. Also most anti-virus software only do system scanning and do not do real-time system monitoring, and the ones that do offer real-time system monitoring may not always catch viruses getting installed on the computer.
2. Keep anti-virus software up-to-date with the latest virus definitions. Just having an anti-virus software installed on your computer is not enough to protect you from the latest virus and computer threats. Keep your anti-virus definitions up-to-date with the latest virus definitions. It is recommended to run anti-virus definitions updates on a daily basis to ensure the most effective anti-virus protection.
3. Keep your operating system up-to-date. This means run those pesky Windows Updates whenever your computer prompts you to. Updates oftentimes contain security patches and fixes that have been identified by the software distributor as vulnerabilities. It is best to set your computer to automatically update at a time that you would most likely not be using your computer, such as 3AM. Just remember to leave your computer on and connected to the Internet overnight to install these critical updates.
4. Only open email attachments from trusted sources and in believable situations. Most people get computer viruses by downloading attachments to emails. The attachments can seem legitimate such as a attached document, media file, or picture sent to you from friends or family. However you should be very careful not to download a virus. Sometimes friends, family, or coworkers email accounts can get hacked and will send out malicious software. Always check the file extension that is attached to an email before downloading it onto your computer. If the file extension is a .exe, .bat, .msi, .zip, .msm, .msp, .mst, .idt, .cub, .pcp file this could be a malicious software application. Common pictures file types are .jpg, .png, .gif, .tif, .bmp, and some common document file types are .doc, .docx, .xls, .xlsx, .odt, .txt. If you get an email with a strange file attached to it that doesn’t look like any of these common extensions, it is probably best to first verify with the trusted sender that they indeed sent the file. Also never click on links sent in emails that seem vague like “hey look at this link” or “click here to see my pics”.
5. Never install programs from the Internet that claim to fix a computer issue. While it may seem like a good idea to ask “Google” to fix your computer issue for you. Unfortunately most websites that claim to fix a computer issue by installing a program are not legitimate and are likely just fishing websites to get spam-ware, and other malicious software installed on your computer. Always take your computer to a legitimate computer repair business to fix your computer issue, and never search for a fix using a software program from the Internet.
6. Never illegally download pirated software, music and movies. Most illegal pirating networks, file sharing networks, and file link website will contain malicious software disguised as the newest software, movies or pop music albums. Always purchase software, music, and movies legally to avoid getting a virus from these untrusted file sources.
7. Do not try to install extraneous video and audio codecs. Sometimes you may find a file that has a strange extension. It seems logical to try to find a audio or video codec, or other program that could read this extension, however it is more likely that you would download and install a virus than the actual solution for your file type.
8. Do not install programs that claim to enhance the performance of your computer. There are some programs online that will claim to speed up your computer, or enhance the performance of your computer, or even promise to enhance the graphics capabilities of a computer. These are most likely untrusted websites that try to trick you into installing spam-ware, ransom-ware, malicious programs, and viruses onto your computer.
9. Do not install illegal software on your computer. You may find yourself in situations where a friend, family or other acquaintance has a “hot” copy of a popular software app like Microsoft Office or Adobe Creative Suite for FREE. If it sounds too good to be true…well then it probably is. Do not be fooled, these types of software cost hundreds to thousands of dollars, and the pirated “hot” copies tend to be packaged with malicious software. Always purchase software legally from trusted software distributors. Never install “hot” or “cracked” versions of a licensed software or service.
10. Do not click on pop-ups! Really, DON’T DO IT! Some pop-ups mimic Windows operating system alerts, and can look very convincing at times. Here are a few dead give-aways that you may have an untrusted pop-up:
- has strange unfamiliar icons
- the error message has improper English
- the pop-up box has a message in it promissing to fix your computer issues
- the pop-up moves around
- the pop-up says your computer is infected with a virus
Even the most cautious computer user can sometimes be fooled into installing a computer virus. If you think you may have a computer virus on your computer, contact South City Computer for a tech visit today.
 Apple computers are not immune to malware vulnerabilities. A new form of malware called “ransomware” is targeting Apple’s Mac OS X operating system. Ransomeware is a computer virus that encrypts important data such as pictures, videos, music, and documents in order to “hold it for ransom” at an unsuspecting victim’s expense. If the victim pays the ransom then, hopefully, they would receive a key to decrypt their data, known as a decryption key. Unfortunately many times there is no decryption key and the victim loses not only their data but possibly up to $700 USD in ransom payment. The ransom payment transaction occurs using an anonymous payment method in order to conceal the identity of the scammer holding the data ransom so that there is no trace. Ransomware is usually spread via email attachments, peer to peer file sharing, and more recently removable devices such as external hard drives and USB flash drives.
Apple computers are not immune to malware vulnerabilities. A new form of malware called “ransomware” is targeting Apple’s Mac OS X operating system. Ransomeware is a computer virus that encrypts important data such as pictures, videos, music, and documents in order to “hold it for ransom” at an unsuspecting victim’s expense. If the victim pays the ransom then, hopefully, they would receive a key to decrypt their data, known as a decryption key. Unfortunately many times there is no decryption key and the victim loses not only their data but possibly up to $700 USD in ransom payment. The ransom payment transaction occurs using an anonymous payment method in order to conceal the identity of the scammer holding the data ransom so that there is no trace. Ransomware is usually spread via email attachments, peer to peer file sharing, and more recently removable devices such as external hard drives and USB flash drives. 
 Cybercriminals claiming to be from Microsoft or an anti-virus company may call an unsuspecting victim on the phone. The victim’s information is usually obtained through publicly available phone directories so they scammer may also know other information such as the victim’s name and address when they call.
Cybercriminals claiming to be from Microsoft or an anti-virus company may call an unsuspecting victim on the phone. The victim’s information is usually obtained through publicly available phone directories so they scammer may also know other information such as the victim’s name and address when they call.  Earlier this year cyber security software company Kapersky announced the discovery of a cyber intrusion that affected many of it’s internal computer systems which initiated a large scale investigation. They believe the virus penetrated their systems through an email attachment sent to an employee at the company. From there the virus moved stealthily through the company’s computer network targeting it’s customer’s computer networks and collecting information. Instead of removing the virus Kapersky monitored the virus on their systems in an attempt to better understand its function and purpose.
Earlier this year cyber security software company Kapersky announced the discovery of a cyber intrusion that affected many of it’s internal computer systems which initiated a large scale investigation. They believe the virus penetrated their systems through an email attachment sent to an employee at the company. From there the virus moved stealthily through the company’s computer network targeting it’s customer’s computer networks and collecting information. Instead of removing the virus Kapersky monitored the virus on their systems in an attempt to better understand its function and purpose. Social media “click bait” targeting has become a big business in recent years. “Click-baiting” is when a publisher posts a link on a social media website like Facebook, Twitter, or Pinterest with a headline that lures people to click to see more, without telling them much information about what the user will really be taken to. Websites like BoredPanda, Buzzfeed, Reddit, College Humor, and Gawker (to name a few) use click bait headlines to lure users to embedded web content surrounded by advertisements. Click baiting has forced Facebook developers to re-evaluate their algorithm for what is considered relevant content, as currently the more clicks a link receives the more likely it is to appear in other users feeds. Wording a link with just the right message in order to get users to click out of the social media website is what “click baiting” is all about. While many of these links take users to relevant content (like this article), there are several new scams also using the tactic to infect computers with malware or attempt to steal personal information.
Social media “click bait” targeting has become a big business in recent years. “Click-baiting” is when a publisher posts a link on a social media website like Facebook, Twitter, or Pinterest with a headline that lures people to click to see more, without telling them much information about what the user will really be taken to. Websites like BoredPanda, Buzzfeed, Reddit, College Humor, and Gawker (to name a few) use click bait headlines to lure users to embedded web content surrounded by advertisements. Click baiting has forced Facebook developers to re-evaluate their algorithm for what is considered relevant content, as currently the more clicks a link receives the more likely it is to appear in other users feeds. Wording a link with just the right message in order to get users to click out of the social media website is what “click baiting” is all about. While many of these links take users to relevant content (like this article), there are several new scams also using the tactic to infect computers with malware or attempt to steal personal information. A new destructive virus known as Rombertik avoids detection from most anti-virus software by making a computer unusable by deleting key files on a computer and filling the hard drive with extraneous bytes of data in order to overwhelm the anti-virus software from detecting it.
A new destructive virus known as Rombertik avoids detection from most anti-virus software by making a computer unusable by deleting key files on a computer and filling the hard drive with extraneous bytes of data in order to overwhelm the anti-virus software from detecting it.  Since 2012 a very sophisticated new form of ransom-ware has been infecting millions of Windows computers. CryptoWall, Cryptorbit, and CryptoLocker or Crypto-malware is a Trojan horse that encrypts files on the compromised computer. The malware uses RSA 2048 bit encryption to scramble important data files using public/private key cryptographic technology making the data files unusable. The victim is instructed to pay a hefty ransom fee ranging from $150 to $750 USD using an anonymous bitcoin payment method to purchase the decryption key that will allegedly decrypt the users files. Even if the user pays the ransom, there’s no guarantee that the attacker will provide the decryption key needed to unlock their files.
Since 2012 a very sophisticated new form of ransom-ware has been infecting millions of Windows computers. CryptoWall, Cryptorbit, and CryptoLocker or Crypto-malware is a Trojan horse that encrypts files on the compromised computer. The malware uses RSA 2048 bit encryption to scramble important data files using public/private key cryptographic technology making the data files unusable. The victim is instructed to pay a hefty ransom fee ranging from $150 to $750 USD using an anonymous bitcoin payment method to purchase the decryption key that will allegedly decrypt the users files. Even if the user pays the ransom, there’s no guarantee that the attacker will provide the decryption key needed to unlock their files.  Lenovo recently released a product security advisory about a man-in-the-middle attack vulnerability that exists on some of the Lenovo Notebook laptop models sold by the company between Jan 2014 until Feb 2015.
Lenovo recently released a product security advisory about a man-in-the-middle attack vulnerability that exists on some of the Lenovo Notebook laptop models sold by the company between Jan 2014 until Feb 2015.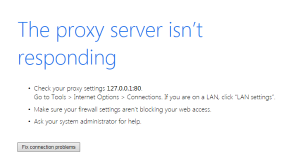 One of the more common computer issues we see because of malware is a misconfiguration Proxy Server connection setting in the browser. You may be able to do a quick fix to get your Internet connection back up and running, however if this has gotten set and you don’t recall doing it, this is probably because your computer is infected with malware or a virus.
One of the more common computer issues we see because of malware is a misconfiguration Proxy Server connection setting in the browser. You may be able to do a quick fix to get your Internet connection back up and running, however if this has gotten set and you don’t recall doing it, this is probably because your computer is infected with malware or a virus. The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer.
The Internet can be very tricky at times, much like the streets of a large city, people can easily be fooled if they don’t use their “street-smarts” in every situation they encounter online. People who let their guard down online can easily be fooled into installing unwanted spamware, ransomeware, malware, virus, trojans, or worms. Avoide the following 10 most common ways our customer’s typically have gotten a computer virus on their computer.